Vulnerability Management: Navigating the Cybersecurity Landscape
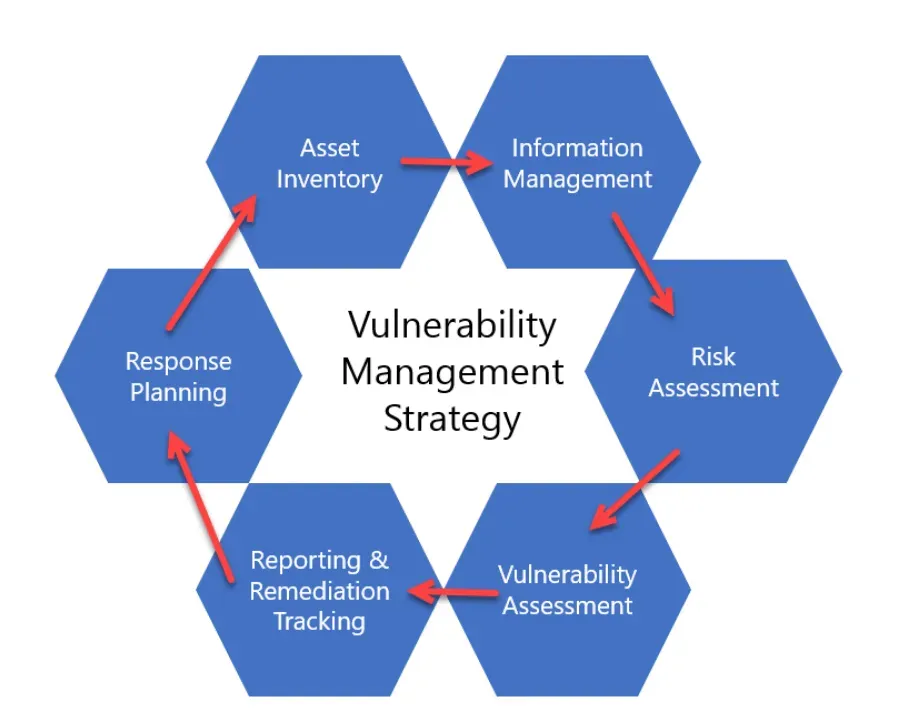
In today’s rapidly evolving digital landscape, **vulnerability management** is essential for safeguarding organizations against cyber threats. With the increasing prevalence of **cybersecurity vulnerabilities** that expose systems to malicious attacks, proactive identification and remediation have become critical. Recent **CISA warnings** underscore the urgent need for businesses to implement robust protocols to manage and mitigate these risks effectively. By closely monitoring metrics like **CVE tracking**, organizations can stay ahead of potential **security breaches** and thwart **identity-based cyberattacks** that could lead to devastating financial consequences. Ultimately, having a comprehensive vulnerability management strategy is no longer optional; it is a necessity in the face of a growing threat landscape.
Vulnerability management refers to the systematic process of identifying, evaluating, and prioritizing weaknesses within an organization’s systems and software. This practice, which includes concepts such as risk assessment and mitigation strategies, is vital for maintaining organizational security. In light of increasing threats, including known exploits and emerging attack vectors, organizations must adopt a proactive stance on threat mitigation and security auditing. Recognizing the scope of potential threats is crucial, as is understanding the implications of neglecting vulnerability assessment. By prioritizing this process, businesses can effectively shield themselves from a variety of digital intrusions and enhance their overall cybersecurity posture.
Understanding Vulnerability Management in Modern Cybersecurity
Vulnerability management is a critical process in the realm of cybersecurity that involves identifying, classifying, remediating, and mitigating vulnerabilities within an organization’s systems. The increase in cyber threats, including recent exploits uncovered in systems like Windows NTLM, has accentuated the importance of a robust vulnerability management strategy. By systematically tracking Common Vulnerabilities and Exposures (CVE), organizations can better defend against potential attacks and ensure compliance with security policies, reducing the likelihood of security breaches.
Furthermore, effective vulnerability management allows organizations to react promptly to CISA warnings or alerts about emerging threats. As we’ve seen recently, identity-based cyberattacks are increasingly sophisticated, with a notable one-third of intrusions stemming from this method. Therefore, continuous vulnerability assessments and timely updates not only streamline security processes but also help in prioritizing which vulnerabilities need immediate attention based on their severity and potential impact.
The Impact of CVE Tracking on Cyber Defense Strategies
CVE tracking plays a pivotal role in forming proactive cyber defense strategies. With the ever-evolving threat landscape, having a structured approach to monitor vulnerabilities allows organizations to stay ahead of cyber threats. By integrating CVE tracking into their security protocols, businesses can create a real-time snapshot of their organization’s security posture, allowing them to address weaknesses before they are exploited by cybercriminals. Recent attacks demonstrated that known vulnerabilities can remain unpatched for long periods, emphasizing the need for vigilance in tracking these risk factors.
Moreover, as cybersecurity vulnerabilities continue to emerge, the effectiveness of CVE tracking relies on collaboration and information sharing among organizations. By leveraging data on vulnerabilities such as those highlighted in Cisco Webex and Oracle Cloud incidents, companies can enhance their security measures and better prepare for potential breaches. This collaborative approach not only fosters a more secure environment but also builds resilience against identity-based cyberattacks that exploit unpatched software and systems.
Responding to CISA Warnings Effectively
In the wake of new cybersecurity threats, responding to CISA warnings is paramount for organizations looking to mitigate risks. CISA alerts often highlight critical vulnerabilities and recommended actions that organizations should promptly adopt. For example, following the Oracle Cloud leakage incident, CISA issued warnings underscoring the necessity for immediate patching and incident response efforts. Organizations that adhere to these warnings are better equipped to prevent breaches and protect sensitive data from cyberattacks.
Additionally, integrating CISA’s guidance into an organization’s overall security framework ensures that teams are prepared and responsive. By regularly conducting drills and updates based on CISA recommendations, cybersecurity teams can reinforce their response mechanisms. This agility not only helps in maintaining compliance with cybersecurity regulations but also builds stakeholder trust through demonstrable commitment to security and an informed response to vulnerabilities.
Navigating the Rise of Identity-Based Cyberattacks
The prominent rise of identity-based cyberattacks represents a crucial threat in today’s digital landscape, accounting for a significant portion of all intrusions. These sophisticated attacks often exploit weaknesses in identity management systems, placing sensitive personal and business information at risk. Organizations must prioritize fortifying their identity verification processes and implementing multi-factor authentication to curtail these attacks. Recent statistics show a shocking correlation between the increased frequency of such attacks and the prevalence of unpatched vulnerabilities.
To effectively combat these threats, organizations should adopt a holistic approach that includes user training, strict access controls, and continuous monitoring of identity access patterns. Investing in advanced security solutions that leverage machine learning can also aid in detecting anomalies in real-time, thus preempting potential attacks before they escalate. With identity-based cyberattacks on the rise, fostering a culture of security awareness through regular training can empower employees to recognize and respond to potential threats.
Enhancing Cyber Resilience through Vulnerability Assessments
Regular vulnerability assessments are fundamental in bolstering an organization’s cybersecurity resilience. By proactively identifying security weaknesses, businesses can prioritize remediation efforts and close gaps that cybercriminals could exploit. Given the rapid evolution of cyber threats, organizations must conduct these assessments frequently to keep pace with the shifting landscape of cybersecurity vulnerabilities, including critical CISA warnings about new threats that may arise without warning.
Moreover, employing automated tools for vulnerability scanning can significantly enhance the efficiency of these assessments. These tools can quickly identify known vulnerabilities associated with CVEs, allowing IT teams to focus on remediation rather than manual detection. This streamlined approach not only saves time but also ensures that organizations remain a step ahead of cyber threats, thereby reducing the risk of security breaches and maintaining operational continuity.
The Consequences of Unpatched Vulnerabilities in Cybersecurity
Failing to address unpatched vulnerabilities can have dire consequences for organizations, leading to severe security breaches and financial loss. With the increase in cyberattacks targeting known flaws, businesses that neglect to monitor and manage their vulnerabilities find themselves exposed to potential exploitation. The fallout from incidents like the recent Windows NTLM exploits underscores the imperative of maintaining updated software and security protocols.
Additionally, the repercussions of these breaches extend beyond immediate financial impacts; they also affect an organization’s reputation and stakeholder trust. In a world where data privacy is paramount, companies that demonstrate a lack of security diligence face not only regulatory penalties but also long-term damage to their brand image. Investing in a proactive approach to vulnerability management is essential for safeguarding both data and reputation in the increasingly demanding landscape of cybersecurity.
Leveraging Technology to Address Cybersecurity Vulnerabilities
Innovative technologies play a pivotal role in addressing cybersecurity vulnerabilities effectively. Solutions such as Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing the way vulnerabilities are identified and addressed. These technologies analyze vast amounts of data to spot anomalies and predict potential exploit scenarios, providing organizations with actionable insights that enhance their cybersecurity posture. By adopting these tools, businesses can significantly reduce their attack surface and bolster their defenses against emerging threats.
Moreover, cloud-based security solutions allow for more flexible and scalable vulnerability management. As organizations increasingly rely on cloud services, integrating comprehensive vulnerability assessment tools within these environments becomes essential. This strategy enables real-time tracking of vulnerabilities associated with applications and platforms. As a result, companies can respond swiftly to security breaches, ensuring minimal disruption to their operations and maintaining compliance with industry standards.
The Role of Employee Training in Vulnerability Management
Employee training is an integral component of a successful vulnerability management strategy. Cybersecurity threats increasingly exploit human error, making it essential for organizations to foster a security-conscious culture among their employees. Regular training on identifying phishing attempts, understanding security protocols, and recognizing the implications of identity-based cyberattacks can significantly reduce the risk of exploitation. By informing employees about the potential consequences of security breaches, businesses can actively engage their workforce in the fight against cyber threats.
Furthermore, organizations can enhance their vulnerability management efforts by conducting simulated cyberattack drills. These exercises allow employees to practice their response to potential breaches, reinforcing their understanding of security best practices and company policies. A well-trained workforce not only minimizes vulnerability exploitation but also serves as a frontline defense, creating a more secure environment for data and critical assets.
Building a Comprehensive Response Plan Against Cyber Threats
Constructing a comprehensive response plan is critical for safeguarding against the myriad of cyber threats faced by organizations today. Such a plan should encompass everything from identifying and classifying vulnerabilities to outlining specific protocols for responding to incidents. This structured approach ensures that organizations can quickly react to CISA warnings and other alerts regarding critical vulnerabilities, ultimately minimizing the likelihood of a successful cyberattack.
Moreover, a well-defined response plan should include procedures for communicating with stakeholders in the event of a breach. Transparency with customers, partners, and regulatory bodies can significantly mitigate damage to company reputation and foster trust even in adverse situations. By including training and continuous refinement of the response plan in regular business operations, organizations can establish a resilient cybersecurity posture poised to adapt to ever-evolving threats.
Frequently Asked Questions
What is vulnerability management and why is it important in cybersecurity?
Vulnerability management is a proactive approach to identifying, assessing, and mitigating cybersecurity vulnerabilities within an organization’s systems. It is crucial as it helps prevent security breaches by ensuring that potential exploits, such as those cataloged in CVE tracking systems, are addressed before they can be exploited by attackers.
How does CVE tracking relate to effective vulnerability management?
CVE tracking is a foundational element of vulnerability management, providing a standardized way to identify and address cybersecurity vulnerabilities. By monitoring CVEs, organizations can prioritize and remediate vulnerabilities that pose the greatest risk to their infrastructure, reducing the likelihood of security breaches.
What are the consequences of neglecting vulnerability management in an organization?
Neglecting vulnerability management can lead to severe consequences, including increased risk of security breaches, data loss, and reputational damage. Attackers often exploit known vulnerabilities, as seen in recent incidents involving identity-based cyberattacks, which accounted for a significant portion of intrusions.
How can organizations respond to CISA warnings about potential vulnerabilities?
Organizations should take CISA warnings seriously by assessing the indicated vulnerabilities in their systems, implementing timely patches, and reviewing their security protocols. This proactive response can help mitigate risks associated with newly discovered vulnerabilities and prevent exploitation.
What role do identity-based cyberattacks play in the context of vulnerability management?
Identity-based cyberattacks represent a critical area of focus within vulnerability management, as they often exploit weak authentication mechanisms. By effectively managing vulnerabilities related to identity and access control, organizations can significantly reduce their exposure to such attacks.
What are the best practices for establishing a vulnerability management program?
Establishing a strong vulnerability management program involves several best practices, including regular vulnerability scans, integration of CVE tracking into security operations, timely patch management, and employee training on cybersecurity risks. These practices ensure a comprehensive approach to mitigating vulnerabilities.
How do recent security breaches highlight the importance of vulnerability management?
Recent security breaches underscore the importance of vulnerability management by revealing how unaddressed vulnerabilities can lead to significant data compromise and operational disruption. Organizations must learn from these breaches to enhance their vulnerability management strategies and prevent similar incidents.
What tools are available for effective vulnerability management?
Some popular tools for effective vulnerability management include Qualys, Nessus, and Rapid7. These tools enable organizations to automate vulnerability assessments, monitor CVE tracking for emerging threats, and streamline patch management processes to enhance overall security posture.
How can organizations prioritize vulnerabilities identified in CVE tracking?
Organizations can prioritize vulnerabilities by assessing their impact, exploitability, and the criticality of affected systems. Using a risk-based approach allows security teams to focus resources on addressing the most critical vulnerabilities first, reducing the likelihood of security breaches.
What is the impact of emerging technologies on vulnerability management?
Emerging technologies, such as artificial intelligence and machine learning, are reshaping vulnerability management by improving threat detection capabilities and automating responses. These technologies help organizations stay ahead of cyber threats and enhance their ability to manage vulnerabilities effectively.
| Date | Title | Source |
|---|---|---|
| 2025/04/18 | CVE Fallout: the Splintering of the Standard Vulnerability Tracking System Has Begun | The Register |
| 2025/04/18 | Cisco Webex Bug Lets Hackers Gain Code Execution Via Meeting Links | Bleeping Computer |
| 2025/04/18 | Events Giant Legends International Hacked | Security Week |
| 2025/04/18 | Fresh Windows NTLM Vulnerability Exploited in Attacks | Security Week |
| 2025/04/18 | Chris Krebs, Who Debunked the 2020 Election Lies, Vows Full-Time Fight against Trump | ars technica |
| 2025/04/18 | Identity-Based Cyberattacks 1/3 of Intrusions, Drop Infostealers | SC Magazine |
| 2025/04/18 | Peter Thiel’s Spy Company Gets into Bed with ICE As Trump Says He’ll Deport US Citizens | Gizmodo |
| 2025/04/18 | Chinese Hackers Target Russian Government with Upgraded RAT Malware | Bleeping Computer |
| 2025/04/17 | Anonymous Leaks Kremlin Data, but It Could Be Old News | KyivPost |
| 2025/04/17 | CISA Warns of Increased Breach Risks Following Oracle Cloud Leak | Bleeping Computer |
Summary
Vulnerability management is crucial in today’s digital landscape as organizations face an increasing number of cyber threats and vulnerabilities. Recent reports highlight significant incidents, such as the Cisco Webex vulnerability that allows hackers code execution via meeting links and widespread identity-based cyberattacks comprising one-third of intrusions. The rise in such vulnerabilities necessitates a strategic approach to vulnerability management that integrates timely tracking, assessment, and remediation processes to safeguard sensitive information and maintain system integrity.




